In our digital age, the need to make rapid decisions on cybersecurity investments has never been more critical. Nowhere is this urgency more evident than in the healthcare sector, where the risk of cyberattacks is a staggering 300% higher. To compound matters, healthcare organizations grapple with unique challenges that not only heighten these risks but also increase the costs associated with combating digital threats.
Consequently, these organizations find themselves in a race to adopt advanced threat management solutions at a pace far exceeding other industries. However, a significant obstacle looms: Post-mortem surveys conducted by esteemed analysts such as Gartner and MarketsandMarkets reveal that security leaders report an underperformance or failure rate of over 50% on these investments.
This grim reality ushers in an array of risks for healthcare organizations that stand at the forefront of these critical decisions. In this blog, we will delve into the following insights:
- Firstly, we will conduct a comprehensive analysis of the latest statistics concerning cybersecurity breaches in the healthcare sector, providing invaluable insights into the prevailing threats.
- Secondly, we will shed light on why healthcare organizations consider Mean-Time-To-Detection (MTTD) and Mean-Time-To-Response (MTTR) metrics as top priorities.
- Thirdly, we will uncover the underlying causes behind the shockingly high failure rate in establishing successful partnerships to combat these escalating threats.
- Finally, we will introduce our Decision Maps, a groundbreaking approach that accelerates cybersecurity purchasing decisions by 10X, giving our clients a substantial advantage in their battle against cyberattacks.
Let’s dive in!
The breaches keep coming
The healthcare industry is no stranger to relentless cyberattacks, and the need for innovative solutions has never been more evident. Over the past three months, we’ve witnessed, once again, the formidable challenges healthcare institutions face in the realm of cybersecurity. Here’s a snapshot of some prominent incidents:
- Prospect Medical Holdings: A data breach at Prospect Medical Holdings, a healthcare company that operates over 60 hospitals and other healthcare facilities, has exposed the personal information of over 2 million patients.
- Horizon Healthcare Services: A ransomware attack on Horizon Healthcare Services, a large health insurer in New Jersey, has exposed the personal information of over 7 million patients.
Cigna: A data breach at Cigna, a large health insurance company, has exposed the personal information of over 1.5 million customers. - Cypress Creek Health System: A data breach at Cypress Creek Health System, a healthcare system in Florida, has exposed the personal information of over 1 million patients.
- Sutter Health: A data breach at Sutter Health, a large healthcare system in California, has exposed the personal information of over 800,000 patients.
These incidents serve as stark reminders of an escalating trend. In 2022, more than 600 cyberattacks targeted healthcare organizations in the United States alone, resulting in staggering financial losses. Unfortunately, this trend is expected to persist as cybercriminals become increasingly sophisticated in their approaches
Why healthcare is in the bullseye

The incessant barrage against healthcare organizations isn’t coincidental; it’s fueled by the immense value of healthcare data on the black market. Experts widely agree that in 2022, the worth of a single medical record on the black market ranged from $1500 to $1800. This vast discrepancy in value compared to other record types—such as PCI at $350 or social security records at $150—makes healthcare the prime target for cybercriminals.
The 2022 report by the Ponemon Institute on the Cost of a Data Breach revealed that healthcare organizations bore the brunt of 30% of all data breaches in 2021, far surpassing other industries that average 10%. Furthermore, leading non-profit industry organizations have reported alarming statistics from their professional members:
- HIMSS Analytics released a report in 2022 that found that 71% of healthcare organizations had experienced a data breach in the past year. This is an increase from 65% in 2021.
- ISACA’s 2022 State of Cybersecurity in Healthcare report found that 57% of healthcare organizations believe that they are at high risk of a data breach. This is an increase from 52% in 2021. The report also found that 43% of healthcare organizations have experienced a data breach in the past year. This is an increase from 40% in 2021.
Quantifying the impact
In addition to the greater voracity of attacks, the financial impact is also magnified for several reasons. First, healthcare organizations typically store substantial volumes of sensitive patient data, amplifying the scale of breaches. Second, healthcare data breaches cast a long shadow over patients, who face the specter of identity theft and fraud. Third, stringent regulations often bind healthcare entities, resulting in costly investigations and remedies.
As a result, leading analyst have estimated that the average cost of a data breach for a healthcare organization was $10.93 million in 2022, which is significantly higher than the average of $3.86 million for all industries.
Escalating insurance premiums
These sobering statistics, compounded by the intricate challenge of quantifying cyber risk, are significantly influencing the cost and extent of coverage provided by cybersecurity insurance policies. To gain deeper insights into these complexities, let’s juxtapose the impact of ransomware with the trajectory of the cyber insurance landscape.
According to a report by Cybersecurity Ventures, the global ransomware market is expected to grow at a compound annual growth rate (CAGR) of 15% from 2022 to 2025. However, the cyber insurance market is only expected to grow at a CAGR of 7% over the same period. This imbalance creates a widening gap between the rising cost of ransomware attacks and the available insurance funds to tackle them. Consider the following statistics that underscore this reality:
- The estimated ransomware cost was $21.3 billion in 2022, projected to soar past $250 billion by 2025, with healthcare accounting for around 20% of this total.
- The average cyber insurance expenditure for healthcare organizations reached $250,000 in 2022—a figure poised to double to $500,000 by 2025.
- Insurance companies are imposing strict sub-limit on ransomware payments while increasing deductibles. Some insurers have also been adding exceptions to their policies, like for “known” vulnerabilities.
This leaves healthcare organizations in a precarious position, where they are shouldering a much bigger part of the risk of these attacks, while also paying much higher premiums.
The soaring costs of cybersecurity expertise
The repercussions extend beyond immediate financial impact. There’s also a scarcity of qualified cybersecurity professionals in the healthcare sector. Regulatory requirements, legacy systems, and the complexity of securing the mirid of digital assets all contribute to this challenge. This scenario has inflated the average salary of healthcare cybersecurity professionals to $175,000 annually, significantly surpassing the $150,000 norm for other sectors.
The recent Jobs Report by Burning Glass Technologies forecasts a 30% surge in demand for cybersecurity professionals in healthcare for 2023. The strain of these elevated costs and demand, combined with the struggle to find qualified experts, exacerbates the operational vulnerabilities of healthcare organizations.
Deteriorating margins
In the midst of these cybersecurity-related challenges, healthcare organizations are also grappling with shrinking profit margins. On the expense front, virtually every aspect is on the rise. Whether it’s labor costs, infrastructure expenses like technology investments, or the soaring prices of prescription drugs; the delivery of healthcare services is becoming increasingly costly.
Simultaneously, revenues are on the decline. Reimbursements from insurance, which typically constitute roughly 80% of hospital revenue, are dwindling at an annual rate of approximately 3%.
Prioritizing MTTD and MTTR
For these reasons, healthcare organizations grapple with a chicken-and-egg dilemma. On one hand, they need better people, processes, and technology to support much faster Mean-Time-To-Detection (MTTD) and Mean-Time-To-Response (MTTR) activities, thereby reducing business and financial risks. However, budget constraints and limited access to resources hinder their ability to support these initiatives, leaving them in a precarious situation.
Gartner reports that the average MTTD for healthcare organizations is 237 days, compared to 193 days across all other industries. Similarly, the MTTR for healthcare is 88 days, whereas it’s 72 days for other sectors. In simple terms, healthcare entities take more than 20% longer to both detect and remediate threats, significantly contributing to the higher average cost of these breaches.
Harnessing high-value partnerships

In response to these pressing challenges, healthcare organizations are increasingly turning to high-value partnerships to bridge the gap. In the realm of cybersecurity, where the focus is squarely on enhancing MTTD and MTTR, Managed Cyber Threat Service Providers (MCTS) solutions have emerged as the preferred choice for our customers. Gartner defines MCTS as “third-party providers that offer a range of security services, including monitoring, detection, response, and remediation.”
The data underscores the potential value of these solutions, with healthcare organizations demonstrating a higher likelihood of adopting MCTS solutions compared to other industries. A recent study by Frost & Sullivan revealed that 60% of healthcare organizations plan to implement MCTS solutions in the next two years, surpassing the 40% adoption rate in other sectors.
When the right partnership is established the results are fantastic. While these services come at a cost, they effectively address the people, process, and technology deficits vexing healthcare organizations, while offering MTTD and MTTR as a service level agreement (SLA). In turn, most if not all of the related compliance and cyber insurance requirements are also satisfied, making it easer and more affordable to get coverage (keep in mind, some carriers have very specific certifications that need to also be considered).
So far so good, but…
Navigating the complex landscape of MCTS selection
As you can imagine or as you may have already experienced, finding the right partner for such a critical operational role is a complicated task. As with most high risk decisions, security teams are tasked with the burden of fully flushing out the business and technical requirements, creating the RFP (or similar), and performing the analysis—a process that consumes significant time, particularly for teams already stretched thin. For mid-sized healthcare organizations, this endeavor can translate into hundreds of man-hours spanning several months, yet outcomes remain suboptimal.
According to a report by Gartner, approximately 50% of MCTS services perform poorly, and 30% fail altogether. These bleak statistics and their repercussions for organizations contribute to what we refer to as the “doom loop.” In this context, the “doom loop” describes how the risk of an MCTS project failing places an even greater burden on security teams when justifying the project, amplifying an already challenging situation.
Our current processes fails to automate the right things
The challenge isn’t limited to the necessity for rigorous justification; that remains a non-negotiable aspect of the process. The real issue lies in our antiquated methods for analyzing these projects in today’s digital landscape. While we’ve seen progress in some areas, such as streamlining the Request for Proposal (RFP) process, integrating collaboration tools, and gleaning insights from peer reviews through platforms like G2Crowd and Gartner Insights (Crowdsourced Information Brokers), these advancements have done little to genuinely transform this process.
As a result, security teams continue to pour hours upon hours of time into manual research as they read through endless documents, piece together fragmented information, and construct detailed vendor analysis. This not only consumes valuable time but introduces significant project risks, as expressed in the below diagram.
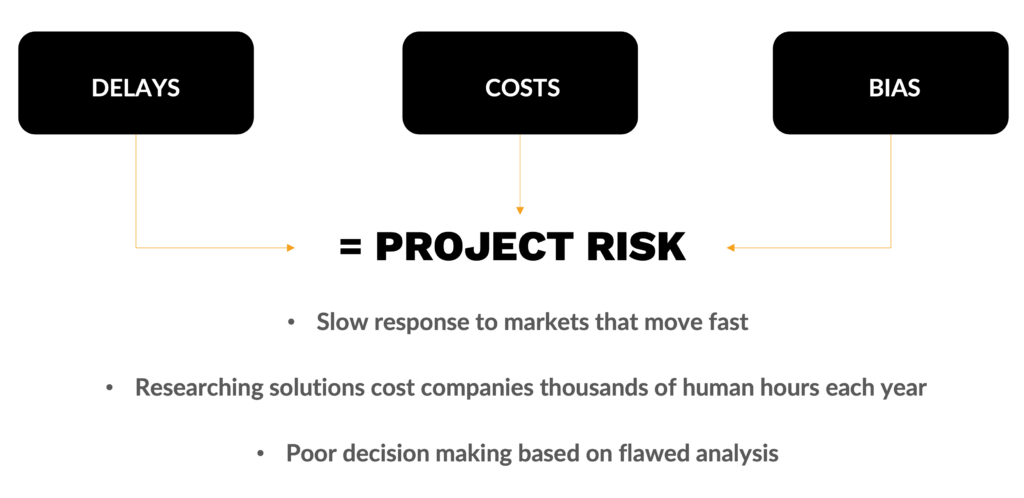
The crux of the matter is rather straightforward: Our existing solutions overlook the fundamental tasks that consume the lion’s share of security teams’ time during the solution vetting process—research and vendor analysis. Without the ability to expedite these critical tasks, the industry’s quest to achieve better outcomes, while accelerating this process, will remain stymied.
Automating MCTS projects with Peer-sourced Decision Analysis
With this perspective, about five years ago Latus embarked on a mission to create a revolutionary collective wisdom system that squarely addresses this solution gap. We’ve christened it Peer-Sourced Decision Analysis (PsDA), aptly named because it focuses on gathering information about how experts have analyzed these decisions, as opposed to exclusively scrutinizing the outcomes of those decisions, as is common with other crowdsourced information brokers. This approach yields a significantly higher-value dataset, empowering our customers to expedite projects in a matter of minutes rather than enduring the traditional months-long process.
As a quick reference, the below chart compares the PsDA approach against the other prevailing models in its ability to automate the research and analysis activities associated with selecting an MCTS partner.
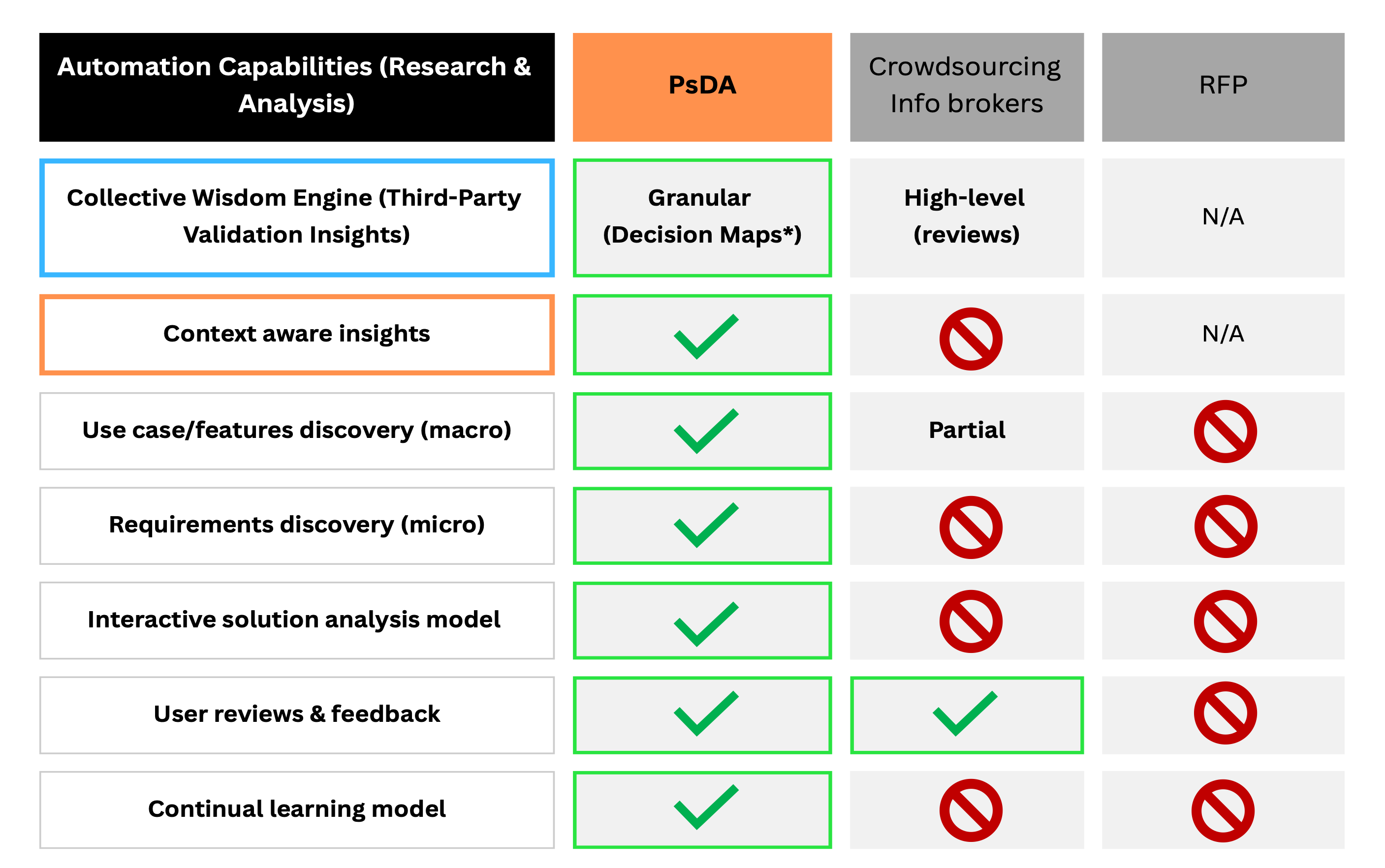
For a much more detailed description of how this works check out our blog on the Importance of PsDA.
MCTS Decision Map is a game changer

At the center of PsDA lies our Decision Map technology, a pivotal innovation in this journey. Think of it as a GPS map designed specifically to engage our collective wisdom engine in support of these decisions. Users have the freedom to explore, customize, and construct their own personalized Maps using the experience of others as their guide. Additionally, from this same interface, users can pivot this Map into a fully functioning MCTS solution analysis model to perform side-by-side vendor evaluation.
This capability is a major leap forward in the realm of cybersecurity decision-making. It not only automates the research and analysis components but also offers an end-to-end workflow for comprehensive vendor assessments. The result? We’re enabling our customers to make these decisions 10X faster while delivering superior results.
For an in-depth exploration of PsDA’s end-to-end analysis capabilities, we invite you to delve into our blog where we draw comparisons to the traditional RFP process.
Conclusion
Modern healthcare organizations demand agile and efficient decision-making processes in light of fast-moving risk management and digital transformation goals, especially when it comes to critical partnerships like MCTS. With the advent of Peer-Sourced Decision Analysis (PsDA), these organizations can bid farewell to the limitations of the existing tools and embrace a new era of accelerated decision-making. Imagine what that could do for your organization.
Are you ready to embrace the digital transformation of your cybersecurity purchasing process?
To learn more and connect with us, visit our solution page on this topic at: https://latussolutions.com/connect/.
Visit our blog page at Latus Blogs
Search
Recent Post
Transforming Cybersecurity Procurement: Exploring the Impact of
- May 24, 2024
- 9 min read
What is Peer-sourced Decision Analysis and why
- December 2, 2022
- 9 min read
Navigating the Future: How Decision Maps Revolutionize
- September 12, 2023
- 12 min read