Introduction
In the fast-paced world of cybersecurity, making the right purchasing decisions can be daunting. The ever-evolving threats and data processing environments leave security teams in a quagmire of complex decision-making. It’s a multifaceted ordeal, where each choice could pivot the organization’s security posture and resilience for better or for worse. Navigating this labyrinth of decisions requires not only diligence but also innovative approaches that can keep pace with the rapid changes.
Enter Generative AI and crowdsourced third-party validation—emerging as beacons of progress amidst this complexity. These technologies promise unprecedented efficiency, offering security professionals new tools to enhance their decision-making processes. But can they truly transform the cybersecurity procurement process?
This blog will delve into the intricacies of cybersecurity decision-making, explore the dual role of generative AI and peer-sourced intelligence, and introduce an innovative approach that has the potential to accelerate decision-making tenfold.
By combining cutting-edge technology with the irreplaceable value of human expertise, we stand on the brink of a new era where decisions are made smarter and faster.
Defining complex decision-making in cybersecurity
Choosing the right cybersecurity solutions is an inherently complex task. Decision-makers face a vast array of options, each presenting unique risks that can significantly impact an organization’s defense and resilience. The challenge goes beyond simply selecting the best technology; it involves understanding how various factors interplay to influence the organization as a whole.
The complexity is further compounded by the rapidly evolving nature of cybersecurity threats. Decision-makers must remain agile, anticipating and planning for these shifting dangers. They are required to sift through a massive volume of information, comparing and contrasting each piece, often dealing with conflicting or incomplete data. This high-stakes environment, characterized by numerous interconnections and constant changes, makes the process of making cybersecurity decisions particularly intricate and demanding.
The duality of generative AI in complex decision-making
Integrating Generative AI into the process of making risk-informed cybersecurity purchases offers a significant advantage by enhancing speed and accuracy in decision-making. However, it’s important to recognize that while AI represents a significant advancement, it is not a panacea.
Strengths of AI in Cybersecurity Decision-Making:
In all cases, complex decision making has a large element of research and analysis since there are many variables to consider. Generative AI excels in these activities for the following reasons:
- Ease of Engagement: By democratizing data science tools, Generative AI has made advanced data analytics accessible to a broader audience. This accessibility facilitates the automation of research and analysis tasks that are typically time-consuming and complex.
- Data Processing Capabilities: With the ability to efficiently process and analyze vast amounts of data, Generative AI excels in synthesizing detailed product specifications, user reviews, and industry insights. This capability enables quicker, more informed decision-making compared to traditional methods.
- Advanced Pattern Recognition: AI is particularly adept at identifying patterns and correlations within large datasets. This ability allows it to predict which security measures will be most effective against specific threats, align with compliance goals, or meet industry best practices.
- Consistency in Evaluation: AI provides a consistent approach to assessing the effectiveness of cybersecurity tools. Unlike human evaluators, who may have subjective biases, AI applies predetermined criteria uniformly, ensuring a fair and objective comparison of options.
The Challenges for AI in this realm
Despite its merits, the Generative AI models available to the public, such as ChatGPT, are engineered for versatility across a broad spectrum of topics and tasks. This “generalist” approach introduces several complications in the domain of cybersecurity solutions assessment, including:
- Efficacy of the Data: The efficacy of data is a cornerstone of Generative AI’s usefulness. However, given that much of this data is harvested from public domains—including social media—the potential for bias or other limiting factors is significant, necessitating rigorous verification that can undercut the benefits of automation.
- Contextual Understanding: in making nuanced judgments about how best to apply this information within the complex, real-world scenario. This gap means that while AI can suggest theoretically optimal solutions, human insight is essential to interpret these suggestions accurately
- Dynamic Adaptation: Cyber threats are not static; they evolve rapidly and so do the related products and services. AI systems trained on historical data may not always identify new forms of cyber controls that deviate from past patterns. This can lead to a gap in recognizing emerging solutions that have not yet been cataloged.
- Ethical and Strategic Considerations: AI lacks the ability to make ethical decisions or understand the strategic goals of an organization. Decisions such as balancing security needs with budget constraints, considering the ethical implications of surveillance capabilities, or aligning with broader business strategies require a level of judgment AI does not possess.
The critical role of human driven analysis in cybersecurity
The limitations of AI often manifest as a lack of “last mile” intelligence, a critical component in making information truly applicable to user-specific scenarios. This last mile analysis, essential during the final stages of selecting technology products and services, involves a comprehensive evaluation that extends beyond mere technical features and marketing assertions. It requires a deep, nuanced understanding of how the technology will mesh with existing systems, fulfill precise organizational needs, and ultimately, deliver substantial value.
Yet, this essential human-driven analysis comes at a high cost for security teams. It requires thorough validation of requirements, assessment of potential solutions, and detailed project justifications—tasks that are both manual and time-intensive. For small, often overburdened teams, this deep analysis extends project timelines and challenges the pace of digital transformation.
Bridging the gap: Using third-party validation as a force multiplier
To ease the burden on cybersecurity teams, the industry has increasingly turned to third-party validation. This approach allows practitioners to learn from their peers to streamline the due diligence process. We’ve written extensively about the goals, sources, opportunities, and challenges of this practice in our blog What is Peer-sourced Decision Analysis and Why is it Important; so we won’t cover those details here. Instead, we’ll focus on this topic from a data perspective to explore the merits of crowdsourcing these insights.
Crowdsourcing has taken off, but…
To leverage the power of third-party validation at scale, leading crowdsourcing platforms like G2Crowd and Gartner’s Peer Insights have become increasingly popular over the past decade. These solutions accelerate purchasing decisions by aggregating review-based data from security practitioners, highlighting their success in implementing and operationalizing security products across various categories. This process is akin to how we use reviews to make decisions in our personal lives.
However, unlike consumer-based decisions, cybersecurity purchasing is a high-risk endeavor that requires extensive due diligence—something reviews alone cannot capture. As a result, these reviews often fall short of truly accelerating decision-making. To better illustrate this, consider the iceberg analogy:
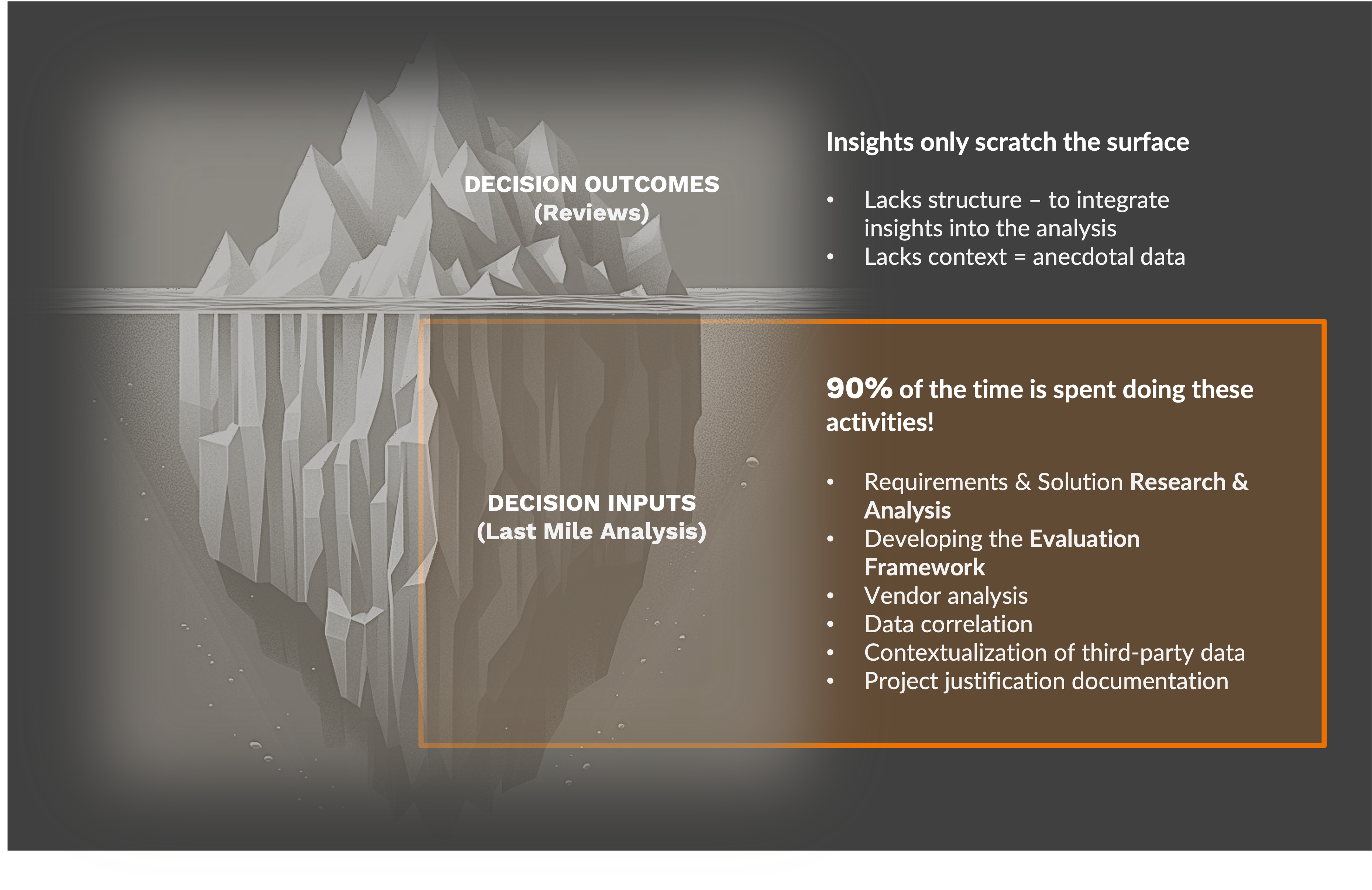
The visible tip represents the reviews of decision “outcomes” provided by today’s crowdsourcing platforms. Limited by their lack of context and structure, they represent only a small portion of the decision-analysis process.
Beneath the surface, however, lies the vast, unseen bulk of the iceberg, symbolizing the extensive research, contextual analysis, and detailed evaluation necessary for making well-rounded decisions. This hidden part includes critical inputs such as developing evaluation frameworks, vendor analysis, data correlation, and project justification documentation.
Harnessing Peer-sourced Decision Analysis for enhanced decision-making
If the goal of using AI and third-party validation is to help organizations make better decisions faster, then focusing these technologies on the most time-consuming activities of the last mile analysis is crucial. Recognizing this need, Latus innovated the next generation collective wisdom systems to address this opportunity, which we call Peer-sourced Decision Analysis (PsDA).
Navigating using our Decision Maps
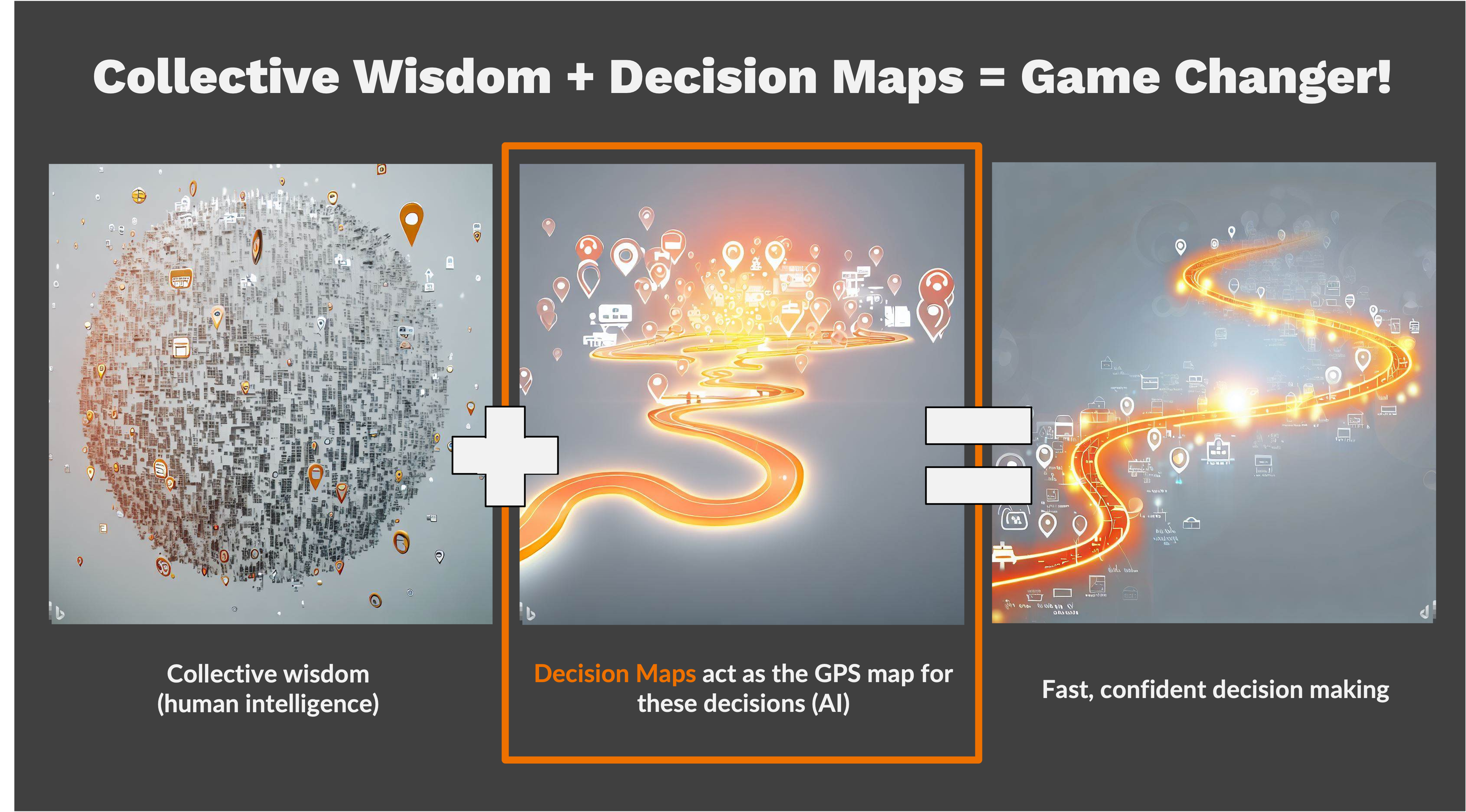
At the heart of the PsDA application is our Decision Map technology, which functions like a GPS navigation system for cybersecurity purchasing engagements. Just as a GPS system allows travelers to plot routes based on current road conditions, traffic updates, and personal preferences, Latus’s Decision Maps offer a similar adaptive pathway for cybersecurity solution vetting. These maps enable users to chart their course through a myriad of considerations, drawing on vast amounts of insights from both AI analytics and the collective wisdom of experts who have analyzed similar decisions.
To further enhance the usefulness, our Map structure enables us to add context to these insights much the same way a GPS map associates user review to route options. It’s a game-changing approach that empowers users explore, customize, and document their purchasing decision criteria in minutes instead of months.
Extending the Value of Decision Maps
Beyond the capabilities of Decision Maps lies their integration into our larger Peer-sourced Decision Analysis (PsDA) application. As users solidify their decision maps, they can seamlessly pivot these maps into a fully functional, side-by-side vendor analysis tool with just a click of a button. This integrated workflow, combined with our advanced business justification module, streamlines and accelerates the solution vetting and project justification process by tenfold.
To learn more about how this compares to the current standard of RFPs, please review our blog Breaking Free from the Constraints of RFPs.
Conclusion
We began this blog with a crucial question: Can AI and crowdsourced third-party validation truly transform the way we analyze cybersecurity purchasing decisions? Throughout our exploration, we’ve examined the strengths and limitations of both the technology and our current methods to gain clarity. Given these insights, it is evident that while AI and crowdsourcing hold significant promise, they also present notable challenges.
To bridge these gaps and fully capitalize on the potential of these technologies, we’ve introduced a new approach called Peer-sourced Decision Analysis (PsDA). PsDA revolutionizes cybersecurity purchasing decisions in two fundamental ways. First, it focuses the crowdsourcing engine on the “inputs” of purchasing decisions rather than the “outcomes,” providing a richer and more valuable data set for analysis. Second, it employs a highly trained AI to perform specific tasks within our Decision Map structure, enhancing the precision and effectiveness of insights generated. These technologies work together like GPS navigation for decision-making, contextualizing expert insights and offering tailored, actionable advice.
In summary, AI and crowdsourced insights, when structured through PsDA and Decision Maps, have the potential to fundamentally transform cybersecurity purchasing decisions, making them smarter, faster, and more effective.
To learn more and connect with us, visit our solution page on this topic at: https://latussolutions.com/connect/.
Visit our blog page at Latus Blogs
Search
Recent Post
Transforming Cybersecurity Procurement: Exploring the Impact of
- May 24, 2024
- 9 min read
What is Peer-sourced Decision Analysis and why
- December 2, 2022
- 9 min read
Navigating the Future: How Decision Maps Revolutionize
- September 12, 2023
- 12 min read