Simply put, Peer-sourced Decision Analysis (PsDA) is the process of gathering intelligence from experts to support complex decision-making...
As a security integrator, we have been helping our clients navigate the complex process of purchasing cybersecurity products and services for 15 years. During that time, we’ve seen the difficulty of these decisions escalate as companies are faced with a multitude of product options across the ever-evolving threat, data processing, and compliance landscapes. This complexity results in a significant increase in the time and effort needed to research and evaluate solutions, which can add up to hundreds or even thousands of man-hours each year.
To help overcome this burden, security professionals are turning to third-party validation. In this blog, we will examine why companies seek these sources, the difficulties they face when gathering this data, and introduce a new approach called Peer-sourced Decision Analysis (PsDA). As a preview, our customers who have adopted our PsDA process have saved a minimum of 80% of the time typically spent on solution analysis. Let’s jump in.
The importance of third-party validation
In the realm of cybersecurity, third-party validation plays a critical role in the purchasing process. There are two main types of validation: expert and peer feedback, and technical validation. However, for the purposes of this discussion, we will focus on the former, as it is an integral part of most cybersecurity purchasing engagements.
Businesses can benefit significantly from this information when it’s collected correctly. Firstly, the data is highly credible because it mainly comes from unbiased feedback given by industry experts and peers. Secondly, when the insights are aligned with the strategic outcomes for the project, they provide great clarity on the decision being made. This enables businesses to make faster, more informed decisions that are backed by expert insights and peer experiences.
There are two primary ways that our customers leverage this data when purchasing cybersecurity solutions:
- Justifying Investments: Since this data is considered reliable, organizations use this information to support budgeting requests as well as long-term planning activities by way of benchmarking against other companies in their industry.
- Maximizing Efficiency: As most companies struggle with limited cybersecurity resources, third-party validation becomes a force multiplier that enables organizations to make faster decisions while achieving better results.
To underscore the importance of this data, Delinea recently surveyed over 900 CISOs and senior decision-makers to understand how they make cybersecurity tech buying decisions. The study found that respondents overwhelmingly cited gauging their efforts in comparison with their colleagues as a top priority.
Link to Delinea study: https://delinea.com/blog/how-it-decision-makers-make-cyber-security-tech-buying-decisio
Sources of third-party validation
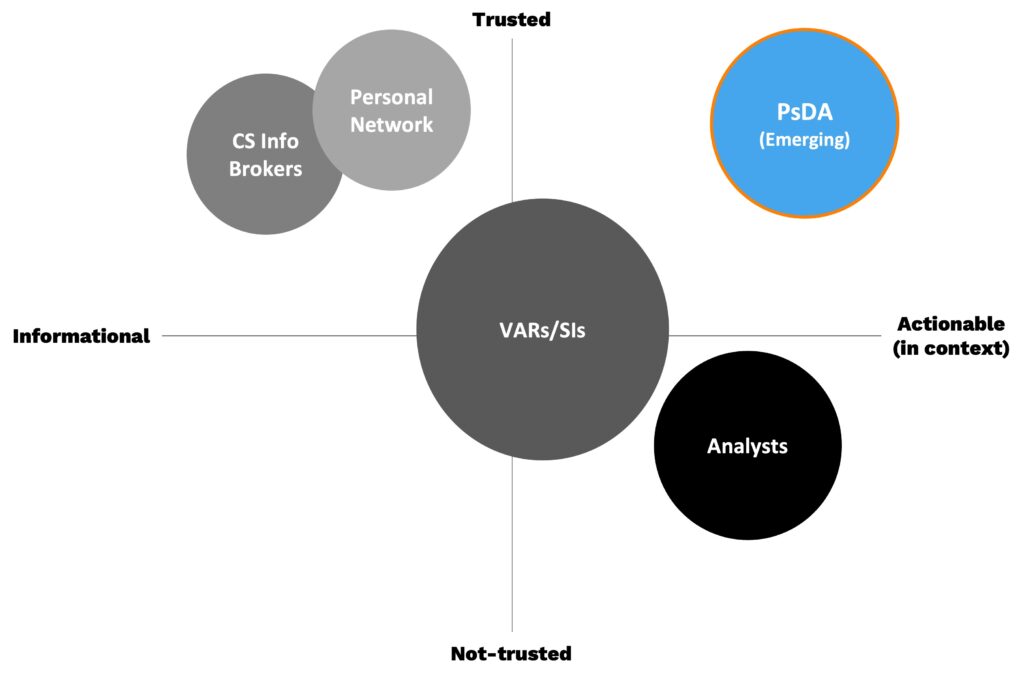
Security professionals rely on four main sources for third-party validation, which vary in terms of the trustworthiness of the source and relevance to the situation (context). These sources include:
- Peers (personal network): Colleagues in the same industry or with similar roles can provide valuable insights and recommendations on products and vendors.
- Partners like VARs and integrators that can share practical experience with working with other companies on similar projects
- Industry experts: Subject matter experts and analysts can provide in-depth analysis and evaluations of products and vendors.
- Software review websites (CS Brokers): Platforms like Gartner Insights and G2 Crowd, which crowdsource reviews of enterprise software products, can provide a wide range of user experiences and feedback.
From a user perspective, the ideal solution would be to learn from peers who have recently made the same purchasing decision and share the same analysis parameters. This means their project goals, data processing environment, security control landscape, and operational maturity would need to be almost identical. In this scenario, since the context can be validated and it’s coming from a trusted source (peers), the users of this data could consider it actionable information. This intersection is represented by the blue circle in the below diagram.
The challenges with engaging third-party data
This “ideal solution” holds great promise for security teams to move a lot faster with better data, but it’s very hard, if not impossible to accomplish. According to Gartner, mid-sized companies spend over 50% of their time researching and analyzing products on third-party validation activities. If you aggregate that across the decisions IT organizations make in a year, it can translate into hundreds, if not thousands, of man-hours of time.
From our 15 years of experience working with customers on these efforts, much of the inefficiencies in this process come down to two main things:
- Data is rarely in context – it’s next to impossible to find the right peers who share similar analysis parameters at the right time. To have any chance of success, security professionals would need to have access to a vast number of similar decision-makers at any given moment. Connecting through crowdsourcing solutions shows promise, but…
- It lacks the necessary structure – having the right structure to collect data is crucial for accelerating the decision process. For buying security products, this would be a specific analysis framework to support the project (decision map*). Without this, third-party data becomes isolated insights that aren’t connected to the strategic goals of the analysis, requiring manual manipulation that adds time and risk to the process. Additionally, users may run into the “chicken and egg” dilemma when trying to structure a comprehensive vendor analysis before gathering third-party validation.
As a result of these factors, third-party validation often becomes just glorified user reviews that are related to the “outcome” of the decision, instead of the “inputs” used to make the decision. This is an important difference, as the latter is the key to unlocking the power of collective wisdom in business-to-business decision-making, while the former is a carryover from how we engage collective wisdom in our personal lives.
The best way I’ve come up with to explain this is to compare it to how we use crowdsourced user reviews when planning a road trip.
You need a map to put review data in context
Making decisions related to a road-trip can be complicated due to various logistical constraints that need to be considered. However, with the combination of GPS maps and user reviews, the planning and execution of trips have been revolutionized. Instead of pouring through maps and researching destinations using paper travel guides, we have outsourced that overhead to data science and the collective wisdom of people who have traveled to the same destinations.
The tight integration between these solutions is what makes it so powerful. The GPS map serves as the source of truth for what users can and cannot do on their road trip, considering factors like timelines, distances, traffic conditions, and more. It also serves as a structure for engaging crowdsourced reviews in the context of possible travel options, enabling users to make faster and better-informed decisions.
Unfortunately, when it comes to engaging third-party validation, the equivalent of the GPS map is missing, making the process manual and time-consuming. It’s like measuring inches to miles on a Rand McNally Road Atlas.
What if security leaders could engage a “project map” to navigate through complex decision-making, similar to how we engage a GPS map for travel? Well, now they can!
Introducing Peer-sourced Decision Analysis
As mentioned in the opening sentence, PsDA is a process for sourcing intelligence from experts to support complex decision-making. In this case, buying cybersecurity products and services.
By utilizing PsDA for customer engagements, we dynamically create “Decision Maps” for how to engage these projects, rather than solely focusing on the outcomes of past decisions. Driven by a ML/AI models that continually get smarter as more users engage with them, we can produce a much more valuable data set that offers several key benefits for our customers:
- The model becomes a cheat sheet for how to analyze the project. Via information sourced from peers who have already made this same decision, users can quickly learn about the key features, the top use cases, the important integration and operational topics, and more. This will move users from starting their discovery to having a very good understanding of these products or services in a matter of minutes instead of months (Decision Map*).
- PsDA produces actionable analysis. Users can customize it to fit their specific needs and then perform side-by-side vendor comparisons against those requirements. This allows for both vendor surveys and detailed vendor discovery to be done with ease.
- PsDA accelerates trust in the analysis. Through process standardization that’s backed by fully contextualized 3rd party validation, users will have a high level of confidence in the results.
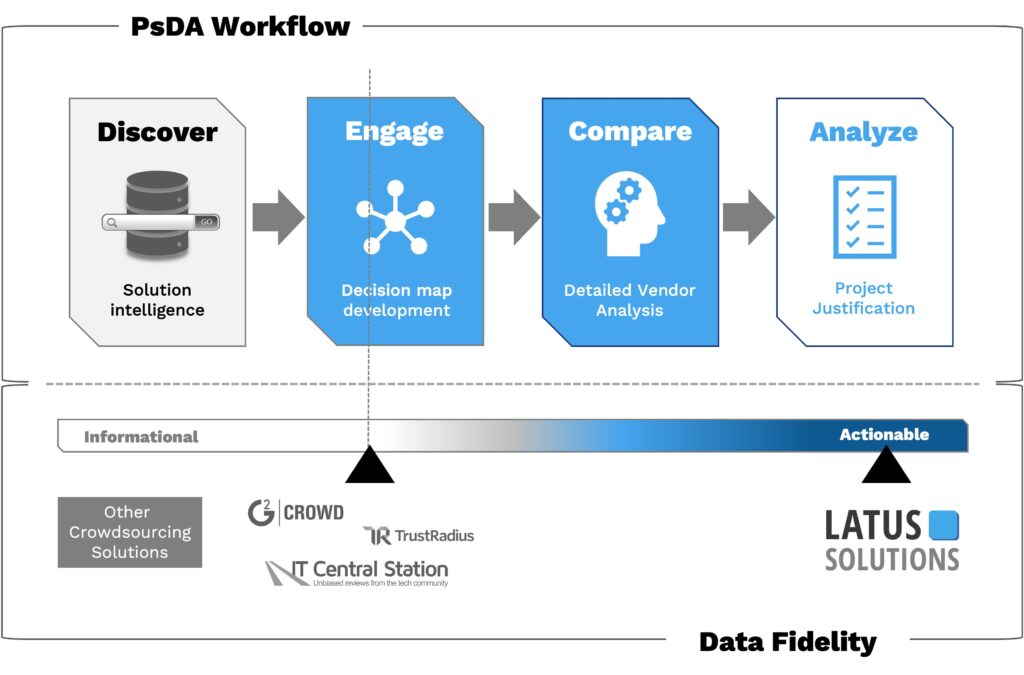
The diagram below illustrates the PsDA workflow and how it compares to other crowdsourcing solutions in terms of analysis capabilities and data fidelity (informational vs actionable).
The results for our customers
To understand the benefit to our customers, it’s important to highlight where we focused our efforts to prove the concept. Knowing we couldn’t take on every project immediately, we set our sights on two of the most important projects for our clients: Managed Detect and Response (MDR) and Endpoint Detect and Response (EDR). Our goal was to help our customers select the best vendor for these solutions using our Decision Maps to guide the way.
After four years of doing it this way, we are really excited about the results, which far exceeded our expectations. Our maps not only addressed the inefficiencies of doing third-party validation (which Gartner equates to 50% of the analysis burden), but they also created a structure to perform the vendor analysis in the same workflow. The combination of these benefits was then measured against the typical hours our clients spend doing these activities across both business and technical resources. Over the past 18 months, we have tracked a saving of 80%+, which is huge!
In the coming months, we will be delving deeper into the various layers of value this approach provides. To stay informed, subscribe to our blog for the latest updates.
If you’re ready to digitally transforming your cybersecurity purchasing process, please contact us at 800-GO-LATUS or klane@latussolutions.com for more information.
For more information on our Decision Analysis process visit our Connect page: https://latussolutions.com/connect/
Search
Recent Post
Transforming Cybersecurity Procurement: Exploring the Impact of
- May 24, 2024
- 9 min read
What is Peer-sourced Decision Analysis and why
- December 2, 2022
- 9 min read
Navigating the Future: How Decision Maps Revolutionize
- September 12, 2023
- 12 min read