Navigating the world of cybersecurity purchasing can be a daunting challenge. Security leaders find themselves grappling with high-stakes decisions amidst the fast paced digital marketplace. Traditionally, companies have relied on the formal or informal Request for Proposal (RFP) process to guide their analysis of solutions and vendors. However, this approach has consistently fallen short in its ability to keep pace with this market, leading to lengthy timelines and disappointing outcomes. It’s time to stop banging your head against this antiquated process and to move into the digital age with a new approach.
In this blog, we will explore why the RFP process is ill-suited for the rapid decision-making. We will also introduce a new approach called Peer-Sourced Decision Analysis (PsDA), which is centered around our “Decision Map” technology. For users, it acts as a visual representation of how leading experts and peers in your industry have analyzed the same purchasing decisions. This collective wisdom become a catalyst for accelerating project timelines by over 80%. So, if you are ready to finally digitally transform your cybersecurity purchasing process, let’s jump in!
The Current State of the RFP Process
Most security leaders have a love/hate relationship with the RFP process. It certainly has its virtues around de-risking security investments through its rigorous and repeatable approach. This is especially important in the realm of cybersecurity, where projects are considered higher risks as they play a crucial role in protecting a company’s brand. Additionally, the RFP process ensures executive-level oversight, fostering transparency, accountability, and effective collaboration throughout the decision-making process. By leveraging the strengths of the RFP process, security leaders can make well-informed decisions that carry substantial credence and support during the project justification phase.
However, administering the RFP process is more arduous than it may appear. The challenges primarily stem from the complexities involved in researching and analyzing projects within the dynamic cybersecurity landscape. Security teams find themselves grappling with vast amounts of information on threats, solutions, intricate data processing environments, and ever-evolving compliance standards. With limited resources, these tasks become overwhelming. It’s no wonder that even getting these projects off the ground takes so much effort.
Recognizing the need for streamlining and optimization, industry participants have endeavored to refine RFP workflows over the years. Collaboration tools, software platforms, end-user review sites, and process optimization have emerged as potential options. While these solutions have helped certain aspects, they often serve as isolated point products that fail to meaningfully accelerate the project timelines.
Using Third-Party Validation to Accelerate the RFP process
In the face of mounting pressure to expedite decision-making, security leaders are increasingly leaning on the knowledge of their peers and trusted experts to fast-track their research efforts. This collective intelligence, known as third-party validation, holds significant power as it comes from unbiased experts who have already made similar decisions. Notably, industry analysts like Gartner and Forrester have also recognized its importance, as it has been highlighted as a critical activity when making cybersecurity purchasing decisions.
But why is this data so indispensable, and how can it revolutionize the solution evaluation process? Drawing from our extensive experience, customers strive to achieve several crucial objectives when engaging in third-party validation:
- Understanding business use cases and related requirements to expedite solution intelligence.
- Seeking input on the vendor analysis process.
- Gathering insights on vendor solutions worth considering.
- Obtaining feedback on users’ experiences in integrating and operating these solutions.
Undoubtedly, when this information is collected and correlated effectively, it can accelerate and enhance the decision-making process significantly.
But... not so fast!
Obtaining usable third-party validation, unfortunately, poses its own set of challenges, which can be summarized into two main issues. Firstly, the data frequently lacks the necessary context to seamlessly relate it to a user’s specific situations. Secondly, it lacks the required structure to efficiently integrate it into the RFP analysis. Consequently, teams invest considerable time in gathering and interpreting this data, making it far from a time-saving activity. In fact, Gartner has estimated that security teams dedicate over 50% of their vendor analysis time to these tasks.
Considering the critical role that third-party validation plays in evaluating cybersecurity purchasing decisions, it becomes evident that the traditional RFP process is ill-equipped to support the digital transformation of these workflows. Instead, a new solution is needed – one that places the collective wisdom of industry experts as the foundation of the solution, rather than treating it as an afterthought.
Introducing Peer-sourced Decision Analysis
In response to a significant market opportunity, Latus proudly introduces Peer-Sourced Decision Analysis (PsDA), a groundbreaking solution that transforms cybersecurity purchasing activities. By harnessing the power of Artificial Intelligence (AI) and collective wisdom in the form of third-party validation, PsDA enables rapid, confident decision-making.
Unlike other collective wisdom solutions like Gartner Insights and G2 Crowd, PsDA takes a unique approach. Instead of focusing solely on user reviews of decision outcomes, we gather insights from users regarding the inputs considered in the decision-making process itself. This approach produces a much higher value dataset that allows us to automate the most time-consuming activities associated with these projects – solution research and analysis.
Automating decision analysis
At the heart of this value lies our Decision Maps. These powerful visualizations embody the wealth of knowledge and insights shared by industry peers and experts who have successfully tackled similar decisions. Think of them as your personal GPS map, guiding you through the intricacies of your cybersecurity purchasing decision. With these maps at your fingertips, you can effortlessly explore options and customize routes to create a map perfectly tailored to your specific analysis needs.
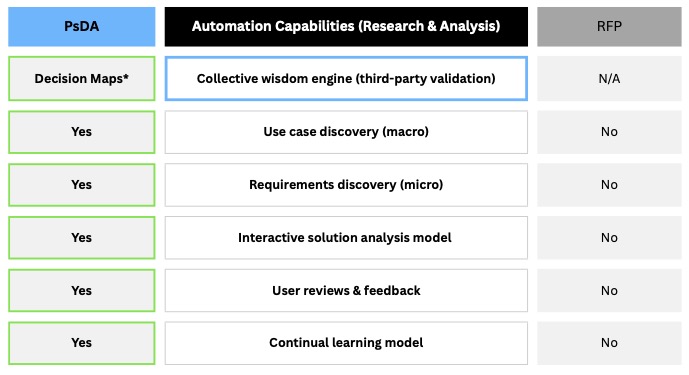
To understand the advantages of our Decison Maps over the traditional RFP process in automating research and analysis activities, refer to the chart below.
These same Maps also serve as the foundation of our analysis standardization capabilities. Since they dynamically capture insights as new users interact with them, they constantly learn and evolve as the market changes, reflecting analysis best practices in near real-time.
Redefining solution analysis and standardization
Additionally, we’ve integrated the Decision Maps into comprehensive, end-to-end solution analysis capabilities. Within a single, unified workflow, users can explore a wide spectrum of options, craft personalized Decision Maps, conduct in-depth side-by-side vendor evaluations, and generate valuable technical and business justification documents.
With this approach, we not only preserve the benefits of the RFP process in the area of analysis standardization, but we significantly enhance them through automation, as illustrated in the chart below.

For a more in-depth description of our platform, check out our blog about the value of PsDA at: What is Peer-Sourced Decision Analysis and Why is it Important?
Conclusion
The cybersecurity landscape demands agile and efficient decision-making processes in light of fast-moving risk management and digital transformation goals. With the advent of Peer-Sourced Decision Analysis (PsDA), organizations can bid farewell to the limitations of the traditional RFP process and embrace a new era of accelerated decision-making. On average, our customers reduce the time spent analyzing cybersecurity purchasing decisions by over 80% while achieving better results. Imagine what that could do for your organization.
Are you ready to embrace the digital transformation of your cybersecurity purchasing process? Connect with us and discover how PsDA can revolutionize your decision-making, enhance your security posture, and propel your organization forward in the ever-evolving threat landscape.
To learn more and connect with us, visit our solution page on this topic at: https://latussolutions.com/connect/.
Visit our blog page at Latus Blogs
Search
Recent Post
Transforming Cybersecurity Procurement: Exploring the Impact of
- May 24, 2024
- 9 min read
What is Peer-sourced Decision Analysis and why
- December 2, 2022
- 9 min read
Navigating the Future: How Decision Maps Revolutionize
- September 12, 2023
- 12 min read







